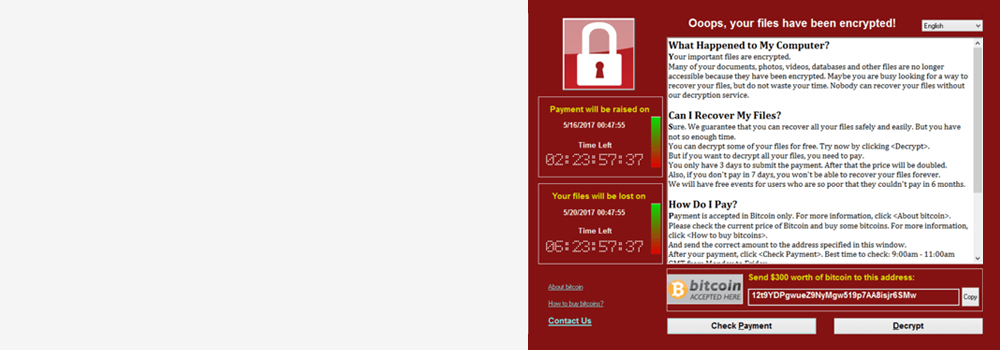
Milton Keynes No. 1 Ransomware Data Recovery Specialist – 25 Years of Experience
At Milton Keynes Data Recovery, we specialize in providing professional ransomware data recovery services for a variety of systems. With over 25 years in business, we have successfully helped clients recover encrypted files, resolve system lockdowns, and address partial encryption caused by the most notorious ransomware strains.
Supported Devices for Ransomware Data Recovery
We recover data from all types of devices, including:
- Laptops
- Desktops
- RAID Servers
- Network-Attached Storage (NAS)
- Standard External Drives
Ransomware Strains We Decrypt
Our forensic data recovery experts have experience handling encryption from the most common ransomware strains, such as:
1. WannaCry
- Description: Exploits EternalBlue vulnerability to spread rapidly across networks.
- Impact: Encrypts files and demands payment in Bitcoin.
2. LockBit
- Description: Highly customizable ransomware known for targeting businesses.
- Impact: Encrypts data with robust algorithms, leaving victims locked out.
3. REvil (Sodinokibi)
- Description: Notorious ransomware-as-a-service (RaaS) strain targeting enterprises.
- Impact: Steals and encrypts data, threatening to leak it unless the ransom is paid.
4. Ryuk
- Description: Often used in targeted attacks against large organisations.
- Impact: Focuses on encrypting critical files to paralyse operations.
5. Conti
- Description: RaaS operation associated with high-profile attacks on healthcare and public sectors.
- Impact: Encrypts files and exfiltrates data for double extortion.
6. CryptoLocker
- Description: One of the earliest ransomware strains to gain notoriety.
- Impact: Encrypts files and demands payment via Bitcoin to decrypt them.
7. Maze
- Description: Combines file encryption with data theft and extortion.
- Impact: Threatens to leak sensitive information if the ransom isn’t paid.
8. DarkSide
- Description: Infamous for its attack on Colonial Pipeline.
- Impact: Uses encryption and data exfiltration for double extortion.
9. Dharma
- Description: Targets small and medium-sized businesses with RDP exploits.
- Impact: Encrypts data and demands payment, often leaving victims without recovery options.
10. Egregor
- Description: RaaS strain that leaks stolen data to pressure victims into paying.
- Impact: Known for targeting large enterprises globally.
11. GandCrab
- Description: RaaS strain that has infected millions of systems worldwide.
- Impact: Encrypts data and provides decryption keys only upon ransom payment.
12. NetWalker
- Description: Ransomware strain targeting healthcare and education sectors.
- Impact: Encrypts files and steals data for extortion purposes.
13. SNAKE (EKANS)
- Description: Designed to target industrial control systems.
- Impact: Encrypts critical systems, disrupting operations in manufacturing and utilities.
14. Avaddon
- Description: RaaS strain that pressures victims with data leaks and DDoS attacks.
- Impact: Encrypts data and leaks it if payment isn’t received.
15. Cerber
- Description: One of the most widespread ransomware strains globally.
- Impact: Encrypts files and uses strong obfuscation techniques to avoid detection.
16. Clop
- Description: Targets entire networks instead of individual devices.
- Impact: Encrypts files and demands high ransom amounts.
17. Zeppelin
- Description: Targets healthcare and tech companies using phishing emails.
- Impact: Encrypts files and requires victims to pay for decryption.
18. Babuk
- Description: RaaS strain that focuses on double extortion tactics.
- Impact: Encrypts files and leaks stolen data to force payment.
19. Ragnar Locker
- Description: Hides its presence by running inside a virtual machine.
- Impact: Encrypts files and demands a high ransom for their return.
20. BlackMatter
- Description: Successor to DarkSide, targeting large enterprises.
- Impact: Encrypts files and threatens to leak stolen data for extortion.
Common Ransomware Issues We Recover From
1. Encrypted Files
- Data locked with strong encryption algorithms.
- We use advanced decryption tools and methods to restore access.
2. Partial Encryption
- Only parts of files are encrypted, leaving data unusable.
- We reconstruct and recover partially encrypted files.
3. System Lockdown
- Entire systems locked, denying access to all files and applications.
- We bypass restrictions to recover and restore data.
4. Corrupted Files Post-Decryption
- Files remain inaccessible after decryption due to corruption.
- Advanced file repair techniques are applied to recover data.
5. Boot Sector Corruption
- Boot sectors encrypted, preventing the system from starting.
- Specialised tools are used to repair boot sectors and recover data.
6. Encrypted Backups
- Local or networked backups encrypted by ransomware.
- Recovery requires deep forensic tools to restore backup files.
7. Ransomware Spread Across Networks
- Infection spreads across multiple devices on the same network.
- We isolate the infection and recover data across all affected systems.
8. Time-Limited Decryption Offers
- Ransomware sets deadlines for ransom payment.
- We provide solutions to recover data without paying the ransom.
9. File Renaming
- Ransomware changes file extensions, masking original data types.
- We identify and restore the original file structure.
10. Data Exfiltration
- Ransomware steals data before encrypting it.
- We address encryption and help mitigate potential data breaches.
Ransomware Issues Requiring Data Recovery
Ransomware attacks are becoming increasingly complex, often resulting in critical data loss. Below are issues caused by ransomware that necessitate professional data recovery:
1. Encrypted Files
- Description: Files are rendered inaccessible due to encryption by ransomware.
- Impact: Data recovery requires decryption tools or professional services.
2. Partial Encryption
- Description: Ransomware encrypts only parts of files, making them unusable.
- Impact: Recovery involves reconstructing the partially encrypted data.
3. System Lockdown
- Description: The ransomware locks the entire system, preventing access to files and applications.
- Impact: System restoration or external recovery methods are required.
4. Deleted Shadow Copies
- Description: Ransomware deletes Volume Shadow Copies to prevent easy recovery.
- Impact: Recovery requires advanced data recovery tools.
5. Ransom Payment Demands
- Description: Ransomware demands payment in exchange for a decryption key.
- Impact: Paying doesn’t guarantee data recovery; professional services are often needed.
6. Double Extortion
- Description: Ransomware both encrypts files and threatens to leak stolen data.
- Impact: Recovery involves dealing with encryption and potential data breaches.
7. Corrupted Files Post-Decryption
- Description: Files remain corrupted even after obtaining a decryption key.
- Impact: Additional recovery techniques are needed to restore data.
8. Data Exfiltration
- Description: Ransomware steals sensitive data before encryption.
- Impact: Recovery must address data theft in addition to file restoration.
9. Boot Sector Corruption
- Description: Ransomware encrypts or damages the boot sector, preventing system startup.
- Impact: Recovery requires boot sector repair and file recovery.
10. Malware Payloads
- Description: Ransomware introduces additional malware to further damage systems.
- Impact: Recovery involves malware removal and restoring affected files.
11. Ransomware Spread Across Networks
- Description: Ransomware infects multiple devices on a network.
- Impact: Recovery requires isolating systems and restoring data across all devices.
12. File Renaming
- Description: Ransomware changes file extensions, masking original file types.
- Impact: Recovery involves identifying and restoring original file types.
13. Delayed Encryption
- Description: Ransomware remains dormant before encrypting files, complicating detection.
- Impact: Recovery is harder due to unnoticed backups containing encrypted files.
14. Data Overwriting
- Description: Ransomware overwrites files during the encryption process.
- Impact: Recovery becomes challenging, requiring advanced forensic tools.
15. Operating System Corruption
- Description: Ransomware damages critical OS files, rendering the system inoperable.
- Impact: Recovery includes OS repair and data restoration.
16. Encrypted Backups
- Description: Ransomware encrypts local or networked backup files.
- Impact: Recovery depends on offsite or unconnected backups.
17. Time-Limited Decryption Offers
- Description: Ransomware threatens to delete the decryption key after a deadline.
- Impact: Recovery requires bypassing encryption or negotiating extensions.
18. Encrypted Database Files
- Description: Ransomware targets SQL, Oracle, or other database files.
- Impact: Recovery involves database-specific decryption and repair.
19. Keyless Encryption
- Description: Ransomware encrypts files without saving decryption keys, making recovery nearly impossible.
- Impact: Requires rebuilding data from remnants or backups.
20. Persistent Ransomware Strains
- Description: Ransomware re-infects systems even after initial removal.
- Impact: Recovery involves securing the system and recovering lost data.
Why Choose Milton Keynes Data Recovery?
- Experience: 25+ years of successful ransomware recovery.
- Advanced Solutions: Cutting-edge forensic tools to handle encryption from modern ransomware strains.
- Comprehensive Coverage: We recover data from all types of devices and ransomware infections.
- No Recovery, No Fee: You only pay if we successfully recover your data.
- Fast Turnaround: Our streamlined processes ensure quick recovery to minimize downtime.
How It Works
Step 1: Contact Us for Free Diagnostics
- Call or email us to discuss your ransomware issue.
- We assess the infection type and provide an initial recovery plan.
Step 2: Forensic Analysis
- We use advanced forensic tools to analyse the encryption method.
- Our team isolates infected files to prevent further spread.
Step 3: Data Recovery
- Using decryption tools and techniques, we recover your data.
- We also repair corrupted files and restore systems to working order.
Contact Milton Keynes Data Recovery Today
Don’t let ransomware disrupt your business or personal data. Contact Milton Keynes Data Recovery for fast, professional, and secure ransomware recovery services.